World’s Easiest and Most Secure MFA
MFA
Secure access for any user and device, to any environment, from anywhere.
Security Score
Get the peace-of-mind only complete device visibility and trust can bring.
Screen Lock
Respond faster to threats with an easy‑to‑deploy, scalable SaaS solution that natively protects every application.
Try Duo For Free!
Book a Demo
Attackers are targeting users, devices and applications to gain remote access! Are you protecting your VPN with Two Factor Authentication?
We can provide MFA for your VPN and reduce the risk of compromised accounts stemming from stolen credentials by 96%.
Intetested to explore the solution? Book a demo with us
Pricing
Get the security features your business needs with a variety of plans at several price points - Our editions cover Duo MFA, Duo Access, and Duo Beyond.
Looking to add Duo to your security ecosystem?
Pricing questions? Check our commerce page or contact us.
We can help you choose the coverage that is right for your business.
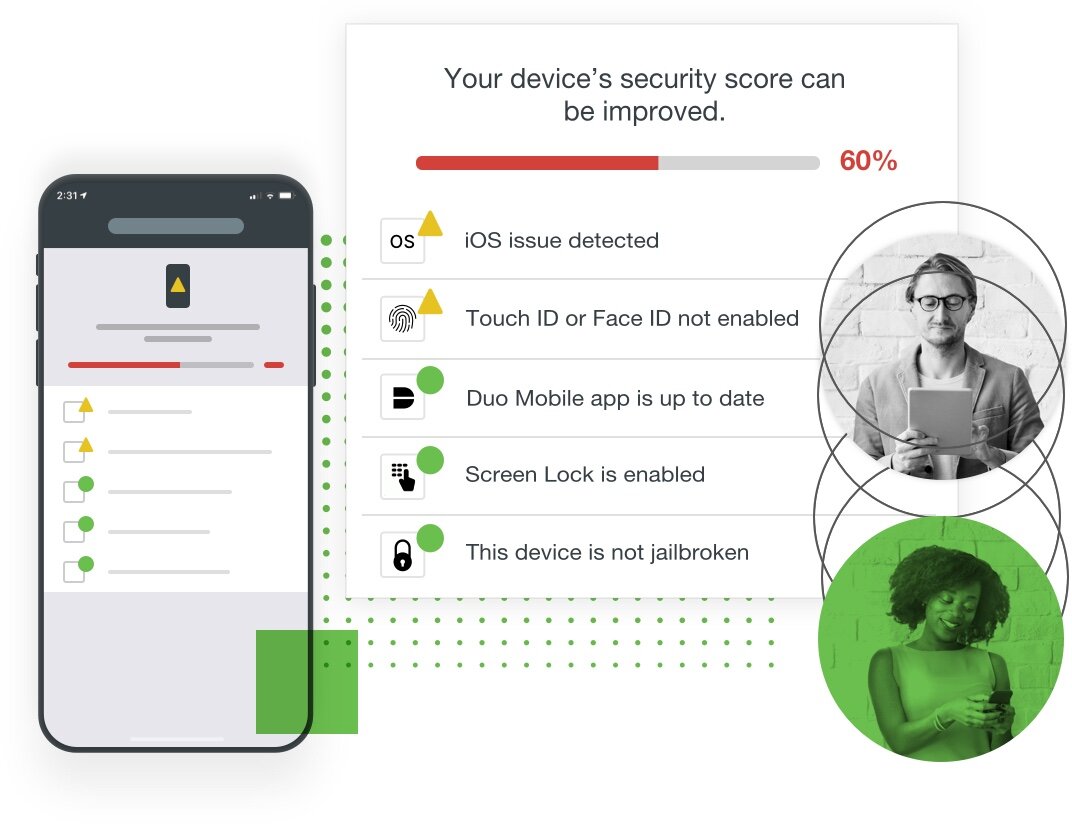
Identify Risky Devices and Behavior
Even a trusted user may be using a device with out-of-date software, leaving them susceptible to vulnerabilities. Duo can automatically flag out-of-date devices and continuously monitor logins from any and every endpoint, saving your administrators upkeep time and resources better spent on your core business objectives.
Verify Trustworthiness of Every Device
Duo's device trust features give you full visibility into the attributes and behaviors of the devices that access your applications.
Duo’s Device Insight inventories every user endpoint and provides data on operating system, platform, browser and plugin versions, including passcode, screen lock, full disk encryption and rooted/jailbroken status. Easily search, filter and export a list of devices by OS, browser and plugin, and refine searches to find out who’s susceptible to the latest iOS or Android vulnerability.
Duo Trust Monitor takes trust a step further by continuously analyzing authentication data, so that you can spot anomalous logins due to changes in device health, security policies, and user behavior.
Whatever it is, the way you tell your story online can make all the difference
Secure Remote Acces Guide.
The 2021 Router ID guide to remote access is now published, get the inside of the latest attack trends and learn how to defend from them.